How Can An Adversary Use Information Available - When adversaries are able to collect enough information, they can piece it. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. Quizlet has study tools to help you learn anything. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail. How can an adversary use information available in public records to target you? Information on programs, deployments, and response procedures.
Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. Quizlet has study tools to help you learn anything. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. How can an adversary use information available in public records to target you? Information on programs, deployments, and response procedures. When adversaries are able to collect enough information, they can piece it. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail.
When adversaries are able to collect enough information, they can piece it. Information on programs, deployments, and response procedures. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail. Quizlet has study tools to help you learn anything. How can an adversary use information available in public records to target you?
How Can An Adversary Use Information Available In Public Records
When adversaries are able to collect enough information, they can piece it. How can an adversary use information available in public records to target you? Quizlet has study tools to help you learn anything. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Public records can be used.
Solved How can an adversary use information available in public
When adversaries are able to collect enough information, they can piece it. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Information on programs, deployments, and response procedures. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and.
How Can an Adversary Use Information Available in Public Records to
In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with.
Solved How can an adversary use information available in
Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate.
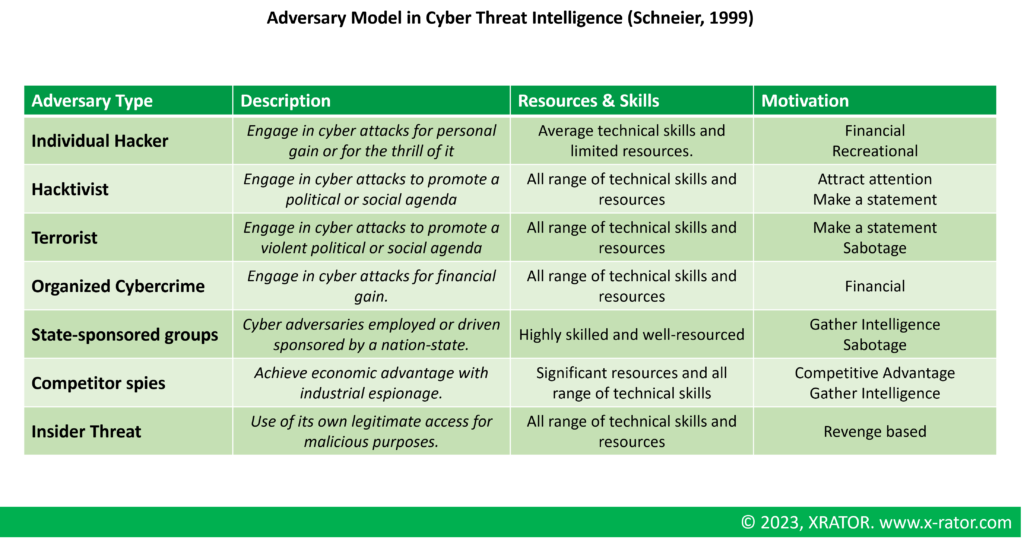
Cyber Threat Intelligence for Data Scientists and Data Engineers
Quizlet has study tools to help you learn anything. Information on programs, deployments, and response procedures. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. How can an.
Presentation Objectives ppt download
In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. Information on programs, deployments, and response procedures. Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. Quizlet has study tools to help you learn anything. How can.
The Risks of Public Records How Adversaries Might Target You
How can an adversary use information available in public records to target you? Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to identity theft and internet. When adversaries are able to collect enough information, they can piece it. Public records can be used by adversaries to target individuals by establishing trust, tailoring.
PAUL CUFF ELECTRICAL ENGINEERING PRINCETON UNIVERSITY Secure
Information on programs, deployments, and response procedures. How can an adversary use information available in public records to target you? When adversaries are able to collect enough information, they can piece it. Quizlet has study tools to help you learn anything. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate.
How Can An Adversary Use Information Available In Public Quizlet
Quizlet has study tools to help you learn anything. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. How can an adversary use information available in public records to target you? Learn how to protect your online identity, avoid cookies, compressed urls, and malicious code, and respond to.
How Can An Adversary Use Information Presentation Objectives Ppt Download
Quizlet has study tools to help you learn anything. When adversaries are able to collect enough information, they can piece it. In this blog, we’ll explore how adversaries use publicly accessible data and what steps you can take to mitigate these risks. How can an adversary use information available in public records to target you? Public records can be used.
In This Blog, We’ll Explore How Adversaries Use Publicly Accessible Data And What Steps You Can Take To Mitigate These Risks.
How can an adversary use information available in public records to target you? Quizlet has study tools to help you learn anything. When adversaries are able to collect enough information, they can piece it. Public records can be used by adversaries to target individuals by establishing trust, tailoring scams, and overwhelming with junk mail.
Learn How To Protect Your Online Identity, Avoid Cookies, Compressed Urls, And Malicious Code, And Respond To Identity Theft And Internet.
Information on programs, deployments, and response procedures.