The Five Pillars Of Cybersecurity Are Availability Integrity - Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,.
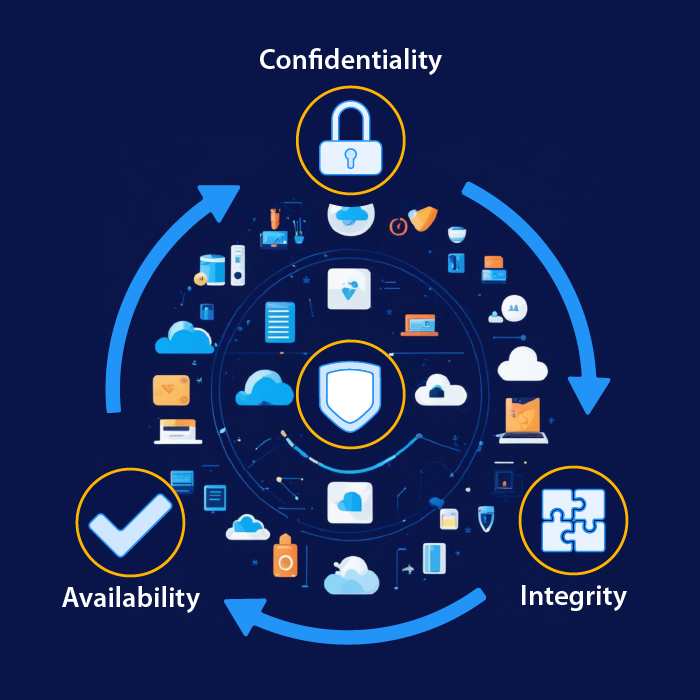
Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive.
Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,.
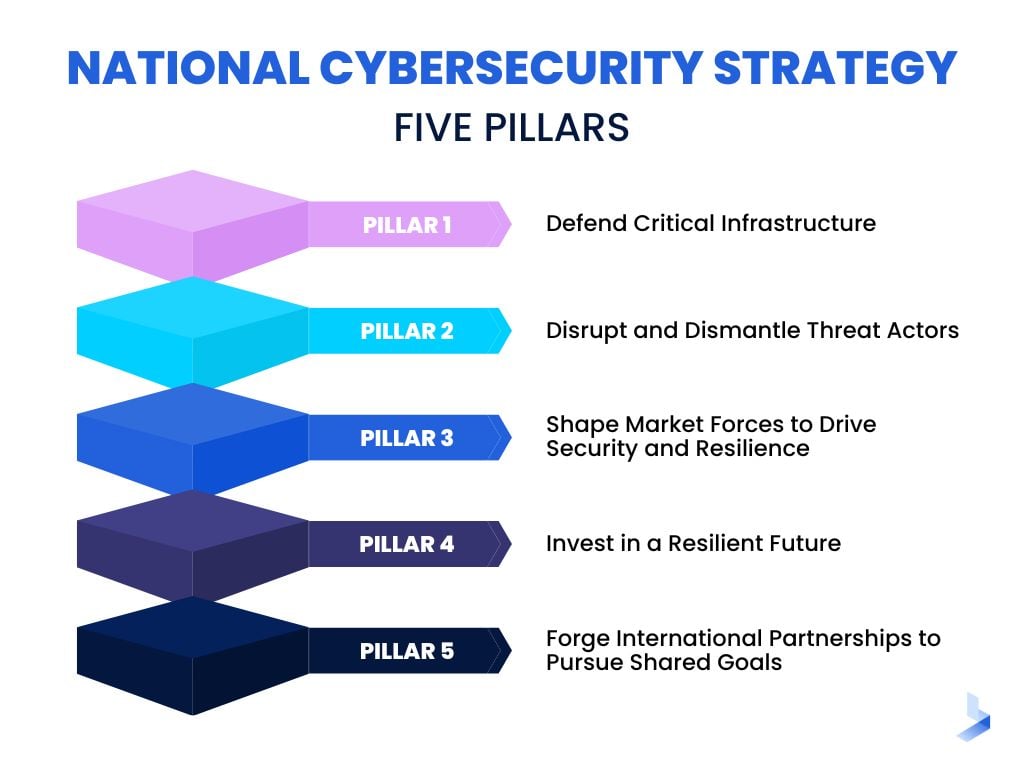
Breaking Down the Biden National Cybersecurity Strategy Key Takeaways
Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive.
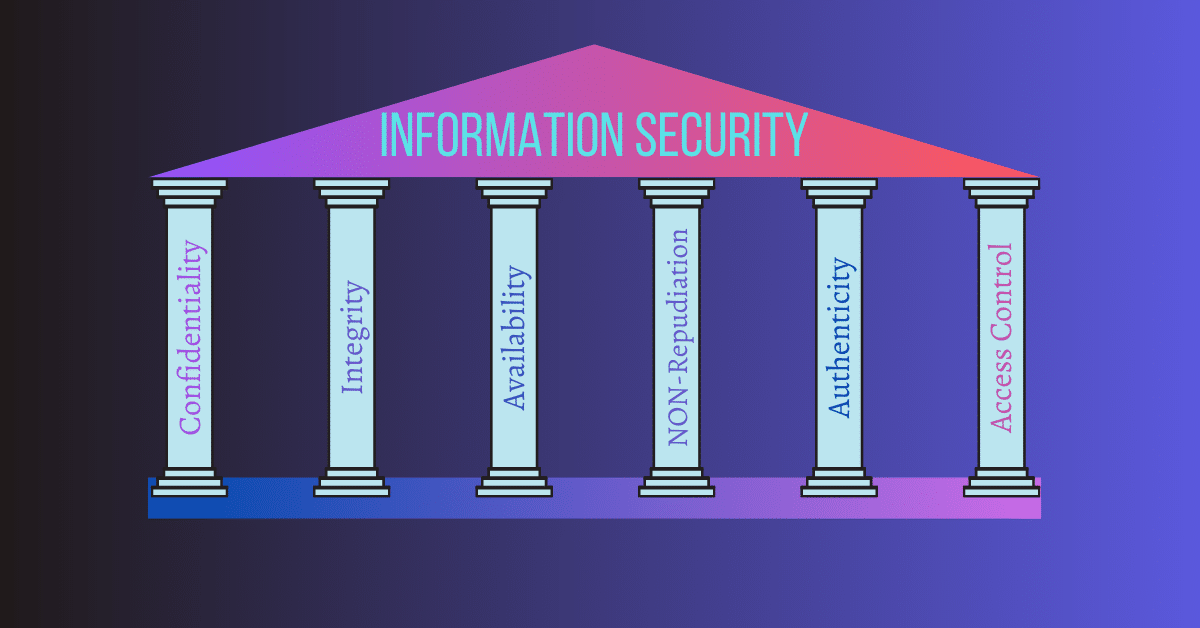
6 Important Pillars Of Information Security
Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info.
5 Pillars of Cybersecurity Planning Preparis
Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info.
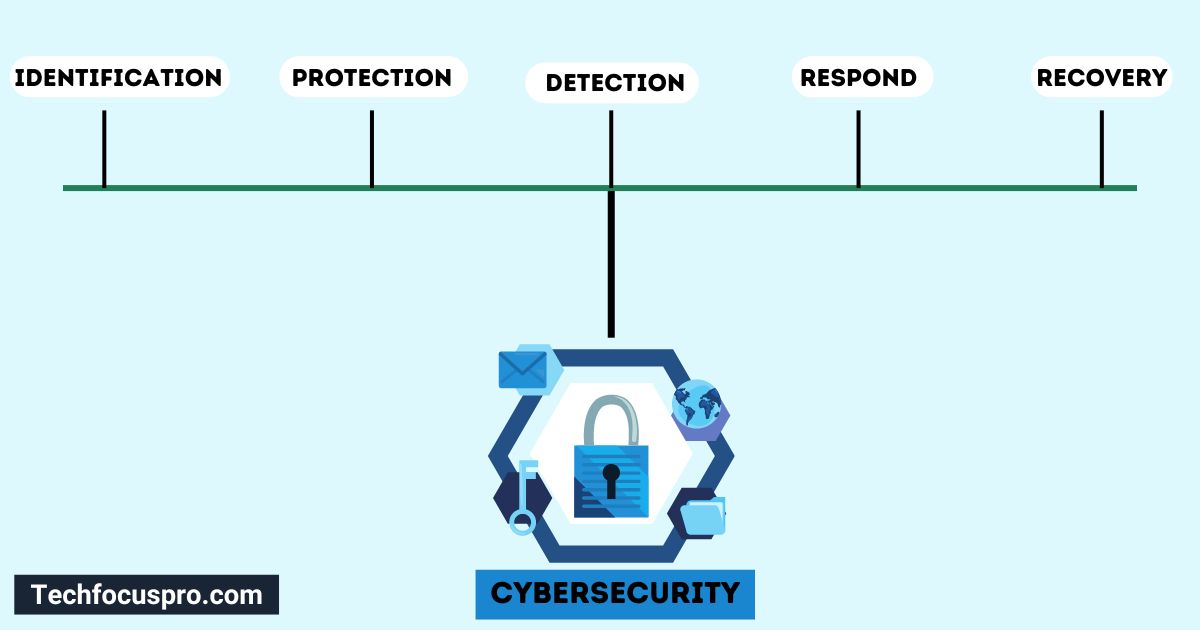
What Are The 5 Pillars Of Cybersecurity? Cybersecurity For Me
Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive.
What are the Five Pillars of Cybersecurity? Tech Focus Pro Best Guide
Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,.
The Five Pillars of Cybersecurity A Brief Guide Tech Hyme
Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,.
Cybersecurity Best Practices for VAT Management VAT4U
Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive.
Confidentiality, Integrity, Availability Key Examples
Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info.
5 Pillars of Cybersecurity How to build a resilient digital fortress
Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive.
The 5 Pillars of Cybersecurity.pdf
Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,. Central to the cissp framework are the five pillars of information security, which serve as the foundation for protecting sensitive. Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info.
Central To The Cissp Framework Are The Five Pillars Of Information Security, Which Serve As The Foundation For Protecting Sensitive.
Study with quizlet and memorize flashcards containing terms like (five pillars of information security) confidentiality, (five pillars of info. Availability ensures that systems remain functional when demanded, integrity guarantees that data is reliable and unchanged,.