How Can An Adversary Use Information Available In Public Quizlet - An adversary can use public records combined with other data sources to craft scams and target individuals. Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. Combine it with information from other data sources to learn how best to bait you with a scam Firstly, they can merge this data with. It is crucial to provide only. Combine it with information from other. How can an adversary use information available in public records to target you? An opponent can utilize details found in openly accessible documents to exploit you in several ways.
Firstly, they can merge this data with. Combine it with information from other data sources to learn how best to bait you with a scam Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. An adversary can use public records combined with other data sources to craft scams and target individuals. How can an adversary use information available in public records to target you? It is crucial to provide only. An opponent can utilize details found in openly accessible documents to exploit you in several ways. Combine it with information from other.
Combine it with information from other data sources to learn how best to bait you with a scam Combine it with information from other. Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. It is crucial to provide only. An adversary can use public records combined with other data sources to craft scams and target individuals. Firstly, they can merge this data with. How can an adversary use information available in public records to target you? An opponent can utilize details found in openly accessible documents to exploit you in several ways.
How Can An Adversary Use Information Available In Public Quizlet
Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. Combine it with information from other. How can an adversary use information available in public records to target you? Combine it with information from other data sources to learn how best to bait you with a scam Firstly, they.
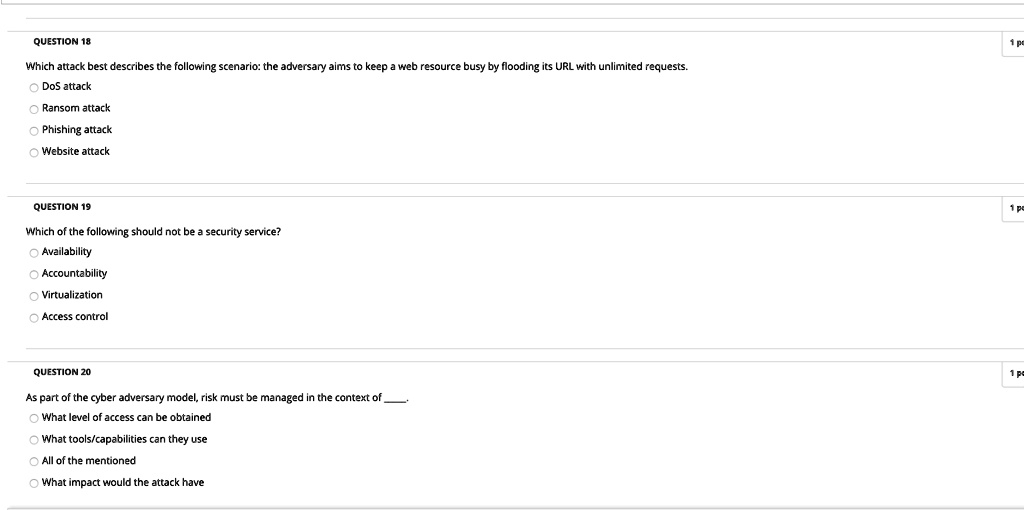
SOLVED QUESTION 18 Which attack best describes the following scenario
An opponent can utilize details found in openly accessible documents to exploit you in several ways. Firstly, they can merge this data with. Combine it with information from other. Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. Combine it with information from other data sources to learn.
How Can An Adversary Use Information Available In Public Records
An adversary can use public records combined with other data sources to craft scams and target individuals. How can an adversary use information available in public records to target you? Firstly, they can merge this data with. Combine it with information from other. It is crucial to provide only.
How can an adversary use information available in public records to
Combine it with information from other data sources to learn how best to bait you with a scam An adversary can use public records combined with other data sources to craft scams and target individuals. How can an adversary use information available in public records to target you? Firstly, they can merge this data with. It is crucial to provide.
Solved How can an adversary use information available in
It is crucial to provide only. An opponent can utilize details found in openly accessible documents to exploit you in several ways. Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. An adversary can use public records combined with other data sources to craft scams and target individuals..
Solved How can an adversary use information available in public
Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. An adversary can use public records combined with other data sources to craft scams and target individuals. How can an adversary use information available in public records to target you? Combine it with information from other. Firstly, they can.
How Can an Adversary Use Information Available in Public Records to
Firstly, they can merge this data with. How can an adversary use information available in public records to target you? Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. An adversary can use public records combined with other data sources to craft scams and target individuals. An opponent.
Cyber Awareness 2024 Quizlet Knowledge Check Dodi Yvonne
Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. An adversary can use public records combined with other data sources to craft scams and target individuals. It is crucial to provide only. How can an adversary use information available in public records to target you? Combine it with.
Cyber Awareness 2024 Quizlet Knowledge Check Dodi Yvonne
Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. Firstly, they can merge this data with. Combine it with information from other data sources to learn how best to bait you with a scam An adversary can use public records combined with other data sources to craft scams.
Presentation Objectives ppt download
Department of defense (dod) cyber awareness challenge 2024 (1 hr) (pre test) how can an adversary use information available in public. Firstly, they can merge this data with. How can an adversary use information available in public records to target you? Combine it with information from other. An adversary can use public records combined with other data sources to craft.
Department Of Defense (Dod) Cyber Awareness Challenge 2024 (1 Hr) (Pre Test) How Can An Adversary Use Information Available In Public.
It is crucial to provide only. An opponent can utilize details found in openly accessible documents to exploit you in several ways. How can an adversary use information available in public records to target you? Combine it with information from other data sources to learn how best to bait you with a scam
Combine It With Information From Other.
Firstly, they can merge this data with. An adversary can use public records combined with other data sources to craft scams and target individuals.