Cyber Security Availability - Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust. Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming.
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
Cyber Security Concept with the Components Availability, Utility
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
Availability As A Goal Of Cybersecurity Training Ppt PPT Presentation
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
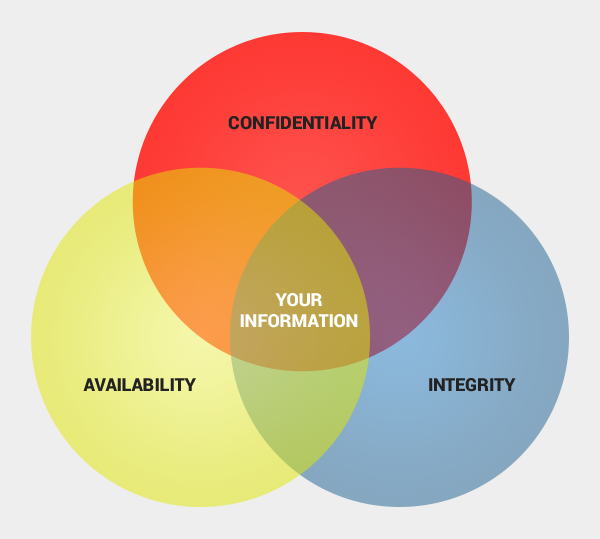
CIA Cyber Security Confidentiality, Integrity, & Availability
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
What's the CIA Triad? The three letters in "CIA triad" stand for
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
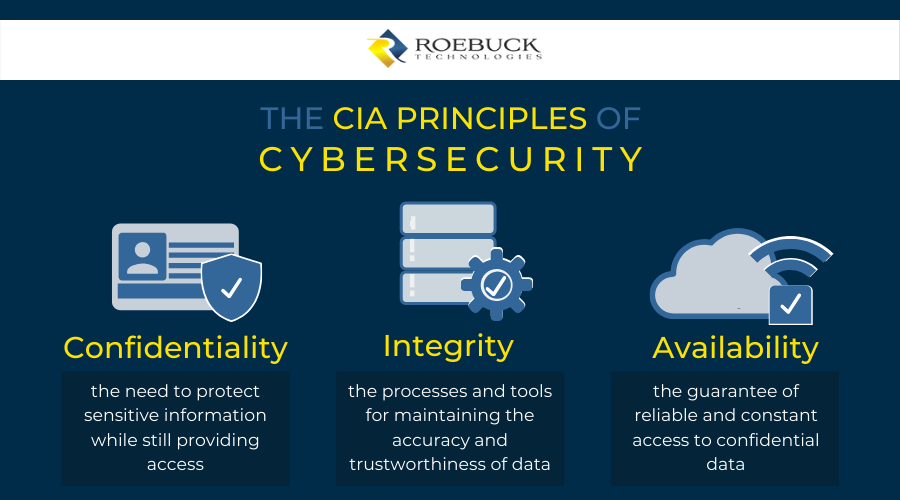
6 Important Pillars Of Information Security
Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust. Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming.
131 Cyber Security Tips that Anyone Can Apply
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
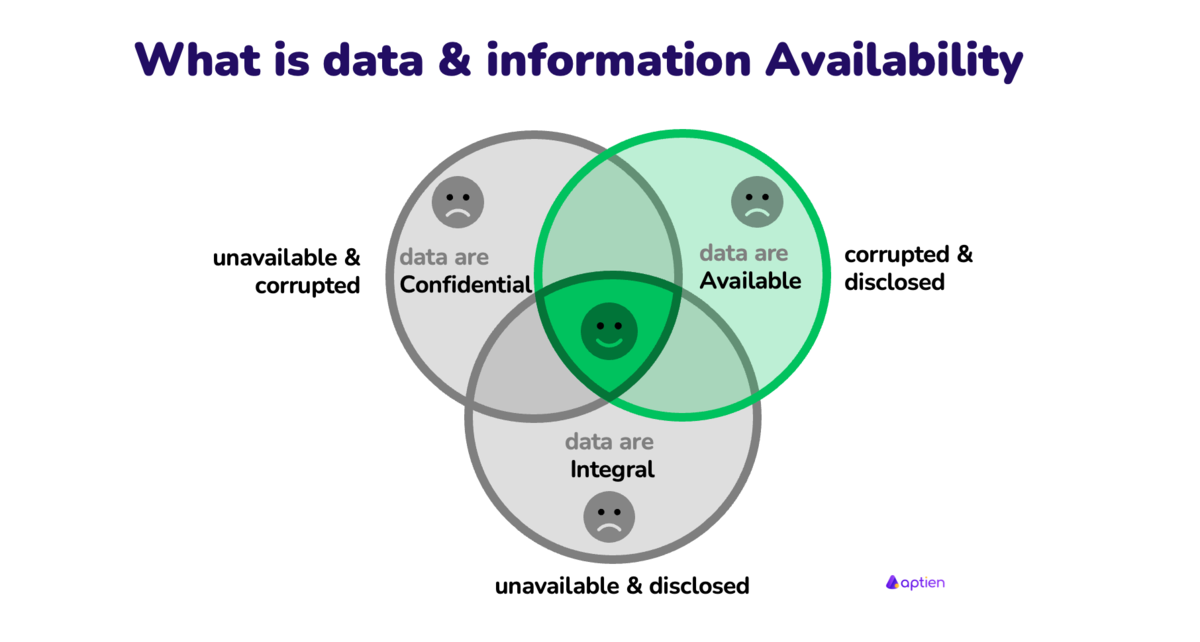
What is Availability Cybersecurity Glossary Aptien
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
COVID19 cybersecurity framework Confidentiality, Integrity, Availability
Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust. Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming.
4. Availability 101. Introduction to availability in cybersecurity
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
6 High Availability Lessons from Cybersecurity Threats SIOS
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming. Downtime, whether due to hardware failure, cyberattacks, or natural disasters, can disrupt operations and erode trust.
Downtime, Whether Due To Hardware Failure, Cyberattacks, Or Natural Disasters, Can Disrupt Operations And Erode Trust.
Vulnerabilities that impact availability can affect hardware, software, and network resources, such as flooding network bandwidth, consuming.